
By leveraging cloud technologies, governments can better manage risks and strengthen their defenses in a fast-changing digital landscape. © Shutterstock
Cloud solutions present significant opportunities for economic growth, digital transformation, and the advancement of technologies like Artificial Intelligence (AI) and the Internet of Things (IoT). Moreover, they can be game-changers for cyber resilience—if we effectively harness their potential.
Yet, cloud adoption remains sluggish in many developing countries. High-income countries score an average of 7.5 out of 10 on the Global Cloud Ecosystem Index, which measures the effectiveness of the enabling environment for cloud adoption. In contrast, low-income countries score only 3.25 on average.
The cloud adoption gap is often driven by concerns about cybersecurity risks, a perceived loss of control over data, and the rising demand for digital sovereignty. As a result, some countries may impose disproportionate data localization requirements, which can inadvertently heighten their vulnerability to significant cybersecurity threats such as ransomware.
In this post, we tackle common misconceptions about cloud adoption and cybersecurity—separating myths from reality and providing actionable insights for governments aiming to navigate the cloud cybersecurity nexus.
Debunking common misconceptions about cloud cybersecurity
Myth 1: On-premises IT systems are inherently more secure
Reality: This belief stems from an outdated cybersecurity model that assumes physical boundaries ensure safety. However, modern cybersecurity practices are moving away from a “perimeter-bound” approach and increasingly embracing Zero Trust Architectures. This paradigm shift acknowledges that the rise of teleworking, cloud computing, IoT, and AI requires a new strategy for managing cybersecurity risks, emphasizing that no implicit trust should be granted to assets or user accounts solely based on device ownership or physical location. Robust technical measures—such as Zero Trust Architectures, multi-factor authentication, and end-to-end encryption—can effectively enhance data confidentiality and integrity, even within public commercial cloud environments.
Myth 2: Cloud adoption lacks clear cybersecurity advantages
Reality: The primary impact of cloud adoption on cybersecurity risk management is the transfer of specific responsibilities from the client organization to the cloud service provider (CSP) through the “shared responsibility model.” While organizations migrating to the cloud retain some responsibilities for cybersecurity risk management—such as access controls—they can benefit from delegating some other key security functions to the CSP, depending on the type of cloud services used.
The shared responsibility model across types of cloud services
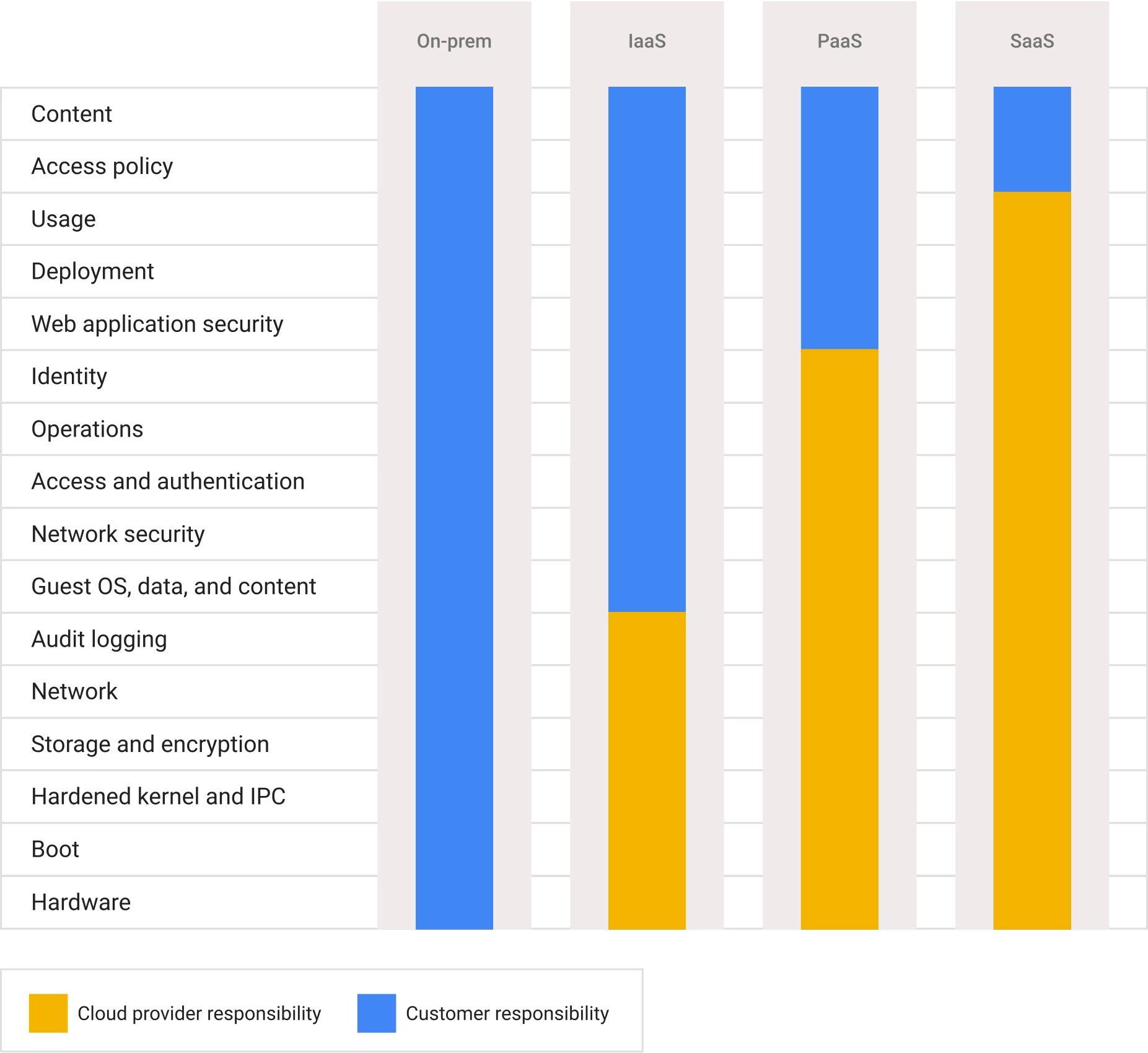
Cloud adoption can be transformative for developing countries with limited resources and digital expertise. The potential cybersecurity benefits are maximized when organizations with low digital maturity—often found in the public sector—adopt hyperscale public cloud solutions. This transition enables these organizations to focus on a smaller set of cybersecurity controls while leveraging the expertise and advanced tools offered by large public cloud providers. These tools include cutting-edge encryption, AI-driven automated threat detection, and continuous 24/7 monitoring.
Myth 3: Legal foreign interference is the main cybersecurity risk
Reality: Concerns about foreign interference and jurisdictional conflicts are often cited as major barriers to cloud adoption. They arise from legal requirements in the countries where cloud providers are headquartered, which can impact the confidentiality and availability of government data stored abroad. While these concerns are valid, they are frequently overstated. A comprehensive national risk assessment would likely reveal that other risks are more pressing.
For most developing countries, the threat of ransomware incidents—like those recently affecting Costa Rica, Tonga, and Indonesia—is far more critical. Moreover, innovative technical solutions such as homomorphic encryption and government-managed encryption keys can enhance data confidentiality. Additionally, large public cloud providers are developing “sovereign cloud” solutions tailored to each country’s unique context, addressing specific concerns related to jurisdictional conflicts.
Myth 4: Technical solutions can solve all cloud cybersecurity issues
Reality: While technical mitigations are crucial, they alone do not fully establish trust in cloud services. Innovative policy measures can provide additional assurance regarding the trustworthiness of these services. For instance, the G20 Data Free Flow with Trust (DFFT) initiative aims to enhance confidence in cloud services by reconciling the objectives of improved cyber resilience, free data flows, and digital sovereignty. The OECD Declaration on Government Access to Personal Data Held by Private Sector Entities (2022) offers an example of how to implement DFFT principles in practice.
Harnessing cloud solutions to strengthen cyber resilience
With these misconceptions addressed, it becomes clear that accelerating cloud adoption should be a priority for developing countries seeking to enhance their overall cyber resilience. But how can they implement this in practice?
Our recent report, Unpacking Cloud Cybersecurity: A Guide for Policy Makers in Developing Countries, provides governments with a set of actionable recommendations to support cloud adoption and maximize its cybersecurity benefits while mitigating associated risks. These recommendations are grounded in good practices from countries like the United Kingdom, the Philippines, India, New Zealand, Singapore, and Pakistan:
1. Implement a risk-based approach to cloud procurement. This involves utilizing instruments such as a cloud-first policy, a cloud marketplace, a data classification scheme, and a risk assessment framework tailored to the specific context of each country (for example, the threat landscape). Together, these tools empower public-sector organizations to effectively integrate cybersecurity requirements when procuring cloud services and select cloud solutions that best fit their needs and context.
2. Adopting hybrid and multi-cloud strategies. These strategies can more effectively mitigate key cybersecurity risks than a “one-size-fits-all” approach that mandates a single cloud deployment model for all government data (e.g., a government-owned private cloud). Hybrid strategies allocate different workloads to various cloud solutions (e.g., private and public clouds) based on the criticality of each workload. Multi-cloud approaches leverage multiple public cloud providers to reduce the risk of vendor lock-in and supply chain dependency.
3. Partner with industry leaders. Collaborating with industry experts is essential for developing a diverse cloud ecosystem. Such partnerships can take the form of framework agreements for public-sector organizations.
4. Invest in international connectivity and cybersecurity skills development. Enhancing capacity in these areas is critical for achieving optimal cybersecurity in cloud environments.
While no solution can guarantee perfect security, adopting cloud services will allow many countries to significantly improve their cyber resilience. By leveraging cloud technologies, governments can better manage risks and strengthen their defenses in a fast-changing digital landscape. These efforts can help developing countries build a stronger foundation for their digital futures.